Hacking is a common term in today's digital age and is often used to describe unauthorised access to computer systems, networks and data.
It is a practice that has been around for decades and has evolved as technology has developed. Hacking can be done for a variety of reasons, including financial gain, espionage, activism and personal fun.
While some hackers use their skills for good, such as ethical hackers who help organisations identify and fix vulnerabilities, others use them to cause harm, steal sensitive information or disrupt critical infrastructure. Understanding the methods and techniques hackers use to find vulnerabilities is critical to protecting our digital assets and privacy.
There are various methods that hackers use to gain access to systems and networks. Here are some of the most common techniques.
Social Engineering:
In doing so, the hacker tries to get people to reveal confidential information or perform actions that are not in their best interest. For example, a hacker might pose as a tech support person and ask for a user’s login details.
Accounts of celebrity Twitter users compromised after vishing scam
In July 2020, Twitter lost control of 130 Twitter accounts, including those of some of the most famous people in the world – Barack Obama, Joe Biden and Kanye West.

The hackers downloaded the Twitter data of some users, accessed the personal messages and called for Bitcoin donations in tweets. Within minutes – before Twitter could remove the tweets – the perpetrator had earned around $110,000 in Bitcoin from more than 320 transactions.
Twitter has described the incident as a “phone spear phishing” attack (also known as a “vishing” attack). The details of the calls are still unclear, but somehow Twitter employees were tricked into revealing credentials that allowed access to the compromised accounts.
After the hack, the FBI launched an investigation into Twitter’s security procedures. The scandal caused Twitter’s share price to plummet by 7% in pre-market trading the next day.
Phishing:
Here, the hacker sends an email or message that appears to come from a trusted source such as a bank or social media site. The message usually asks the user to click on a link or reveal personal information.
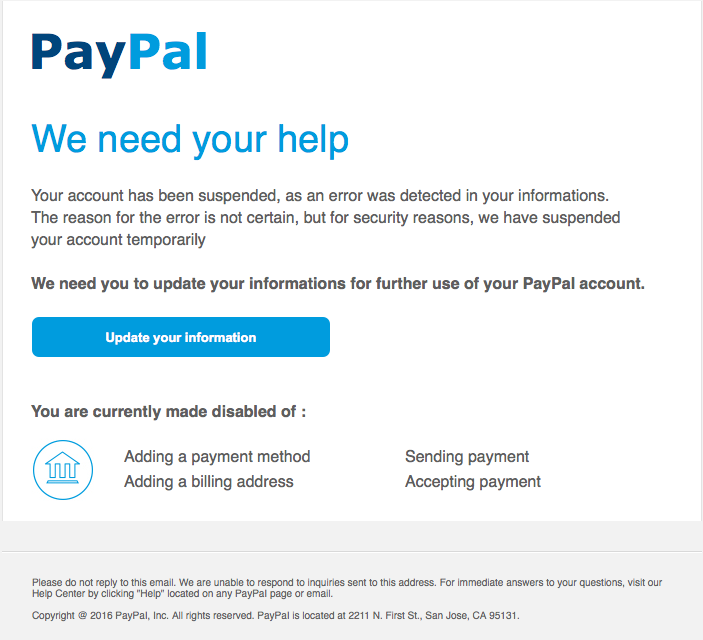
Example,
The victim receives an email from PayPal telling them that their account has been compromised and will be deactivated unless their credit card details are confirmed. The link in the phishing email takes the victim to a fake PayPal website and the stolen credit card details are used to commit further crimes.
Brute force attacks
Here, the hacker tries to guess the password by trying all possible password combinations. This technique can be time-consuming but effective if the password is weak.
If a password is used as a key to open a door, then a brute force attack is equivalent to using a battering ram. A hacker can try 2.18 trillion password/username combinations in 22 seconds and if your password is not complex, your account could be in the crosshairs.

Exploiting vulnerabilities:
Hackers often look for vulnerabilities in software or hardware that they can exploit to gain access to a system. Once they have found this vulnerability, they create a tool for it.
Malware
This is software designed to damage or disrupt computer systems. Malware can take many forms, including viruses, Trojans and ransomware.
Once a hacker has access to a system or network, they can steal data, install malware or use the system to launch further attacks. Therefore, it is important to have strong passwords, keep software up to date and be careful when clicking on links or opening email attachments.
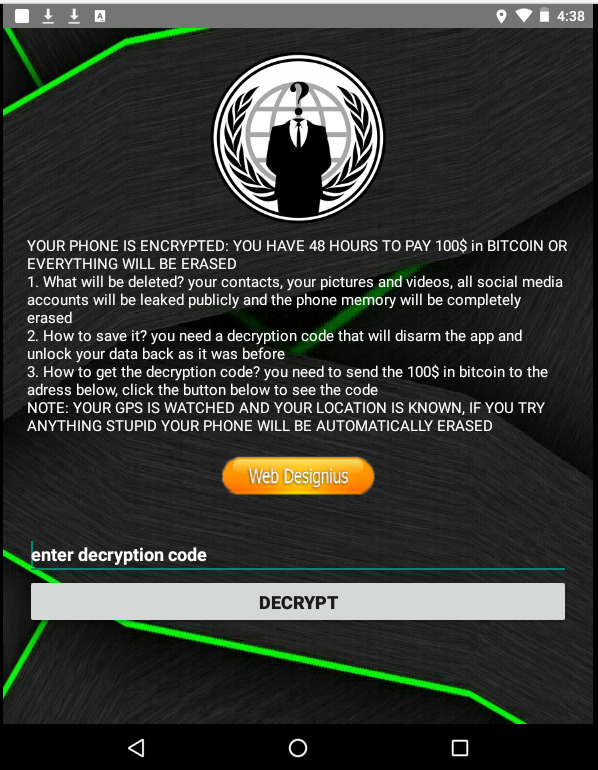
CovidLock, Ransomware, 2020
When everyone almost shut down, hackers became more active than ever. They exploited the fear created by the pandemic (COVID-19). The CovidLock ransomware pretended to offer information about the “disease”.
Once installed, the ransomware encrypts all data on Android devices and denies the user access. To recover your files, you have to pay a ransom of US$100 per device.
What would you do?
Pay or lose your data?
In summary, hacking is a complex process that requires a lot of technical knowledge and skill. There are many different techniques that hackers use, but by understanding these techniques and taking steps to protect yourself, you can reduce the risk of becoming a victim of a cyber attack.
#PRVCYTips
Protecting our data and privacy is more important than ever to avoid hacks and other cyber threats. Hackers are becoming more sophisticated and creative in their techniques, making it harder to protect our digital assets.
By being vigilant and informed about the risks, we can better protect ourselves and minimise the potential damage from a hack or breach of our privacy.
In addition, we should be careful about sharing personal information online and avoid suspicious links or unknown software.
Therefore, we need to take proactive measures to secure our devices, networks and online accounts by using strong passwords, two-factor authentication and regular updates to our software and security tools.
From anywhere, at any time a private digital identity Protected despite AI with PRVCY.world
Protect your privacy and improve your cyber security with our courses! Learn how to protect your personal data and keep your devices safe. Invest in your security and buy your privacy and cybersecurity course today. We’ll help you minimise the risks of AI and other cyber threats.





